There are several methods for implementing secure remote access, but three of the most common are:
- VPN (Virtual Private Network): A VPN is a virtual private network that uses the Internet's public infrastructure to provide secure remote access. A VPN allows remote devices to connect to a private network using encryption to protect communication and guarantee data security.
- SSH (Secure Shell): SSH is an encrypted network protocol that allows one computer to connect to another in a secure and authenticated way. SSH is widely used for remote access to servers and network devices, allowing users to remotely connect to and manage servers and devices using an encrypted connection.
- TLS (Transport Layer Security): TLS is a security protocol that provides secure communications on the Internet. TLS is used to protect web connections, such as e-commerce sites and online banking services, by ensuring that communication between the user and the server is encrypted and authenticated. TLS is widely used in many applications and services to provide communications security.
Organizations are subject to a number of potentially emergency situations, such as disease, floods, hurricanes and power outages. It is crucial that business continuity plans are established in order to ensure that the organization's operations can be maintained in the face of adversity and be prepared to deal with possible disasters.
Understand the importance of secure remote access to maintain the business continuity plan.
Summary
Remote Work Support
Firstly, the ability to support remote working is essential to ensure business continuity and security with remote working.
In this sense, next-generation firewalls from FortiGate (NGFWs) have built-in support for virtual private networks (VPNs) IPsec, in order to allow remote employees a connection of secure remote accessConnection to the company network.
With the protection of endpointprovided by FortiClientWith FortiAuthenticator, organizations can not only securely support remote work, but also maintain business continuity.
The ability to offer secure remote working support is an essential component of any organization's business continuity plan, especially disaster recovery.
In addition, the FortiGate's NGFW have integrated support for IPsec VPNsThe aim is to provide a secure connection for employees working in alternative workplaces.
Secure remote working
Secure remote working with FortiGate and FortiClient Endpoint NGFWs
Primarily, IPsec and SSL VPNs integrated into all FortiGate NGFW, offer a flexible deployment. In other words, remote users can take advantage of an experience without determining the client, as well as gain access to additional features through a robust Endpoint integrated into the security solution of the FortiClient endpoint.
Above all, Fortinet solutions have been designed to be easy to use from the initial purchase to the end of life. In addition FortiGate NGFW and the Access Point FortiAP include "zero touch" deployment functionality.
As a result, devices deployed in remote locations can be pre-configured before shipment, thus enabling automatic on-site installation, which guarantees business continuity and home office support.
Security Fabric Fortinet
Surprisingly, with the Fortinet Security Fabric, all of an organization's devices, including those deployed remotely to support remote working, can be monitored and managed from a single dashboard.
What's more, with a FortiGate NGFW or FortiManager centralized management and deployed at a company's headquarters, the IT team can obtain visibility total of all connected devices, regardless of the deployment situation.
Certainly in the event of a natural disaster or other event that interrupts business operations, an organization must be able to quickly transition to a fully remote workforce. In this respect, Table 1 shows the number of simultaneous VPN users that each model of the FortiGate NGFW can support it.
Other resources
Other Features for Secure Remote Access
Firstly, in addition to offering encryption of data in transit via a VPN, the solutions Fortinet offer several other features that can help your organization protect remote work. These features include:
| Model | Simultaneous SSL VPN users | Simultaneous IPsec VPN users | Managed FortiAPs (Tunnel mode) |
| 100E | 500 | 10,000 | 32 |
| 100F | 500 | 16,000 | 64 |
| 300E | 5,000 | 50,000 | 256 |
| 500E | 10,000 | 50,000 | 256 |
| 600E | 10,000 | 50,000 | 512 |
| 1100E | 10,000 | 100,000 | 2,048 |
| 2000E | 30,000 | 100,000 | 2,048 |
| All Larger Models* | 30,000 | 100,000 | 2,048 |
| *3300E supports 1,024 Tunnel Mode APs |
Use Cases - Remote Work
Firstly, we know that not every employee in an organization requires the same level of access to company resources when working remotely.
In this sense Forti One IT together with Fortinet, is able to provide customized home office solutions for all remote workers:
At the same time, basic remote workers can connect to the organization using FortiClient integrated into VPN and verify your identity with FortiToken for multi-factor authentication.
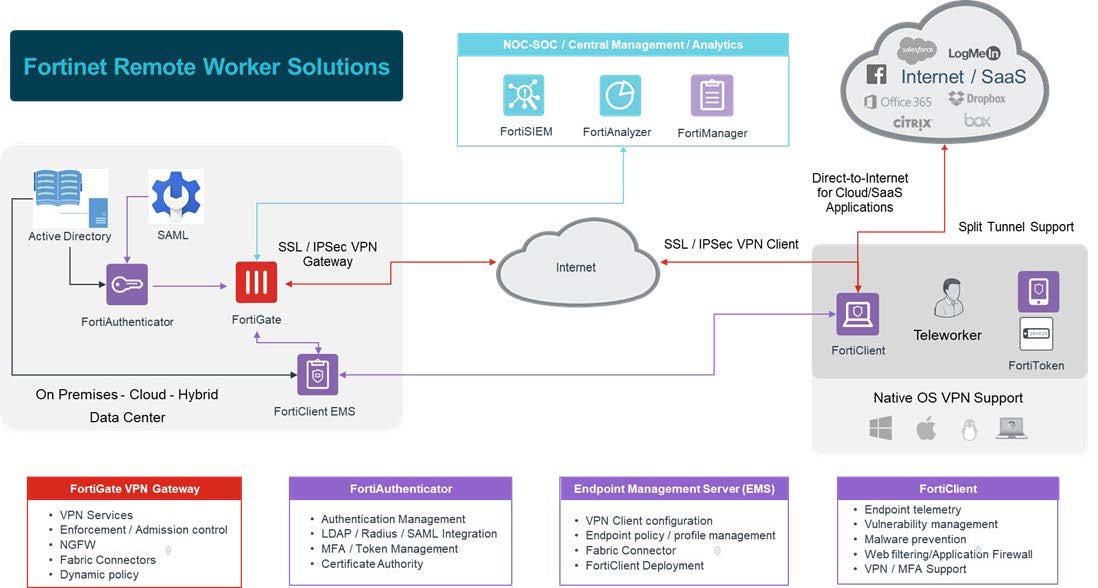
This not only includes the ability to operate in several parallel IT environments, but also the inclusion of system administrators, IT support technicians and emergency teams.
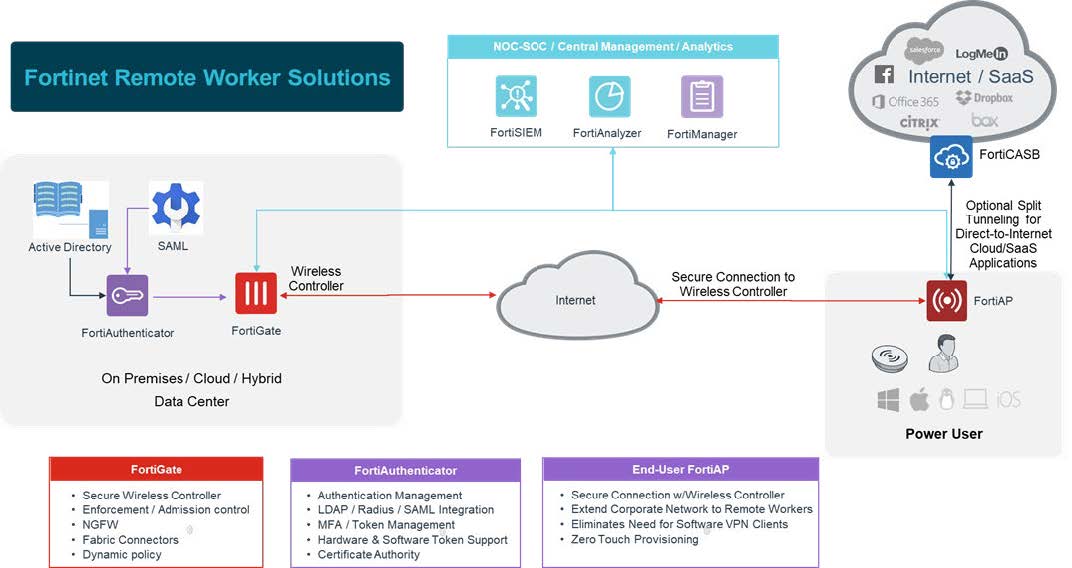
In short, for these users the deployment of an access point FortiAP in the alternative workplace, provides the level of access and security they require. As a result, it provides secure wireless connectivity as well as a secure tunnel to the corporate network.
Just to illustrate, the FortiAPs can be deployed with ZTP (zero-touch provisioning) and will be managed by FortiGate NGFWs in the office. For example, if a tcorporate phone needs to be deployed, it can simply be connected to FortiAP for connectivity back to the main office.





